Let's Encrypt, Certbot and ACME
Short history, and a long future
2019 / @joohoi
whoami
Joona Hoikkala
- @joohoi (pretty much everywhere)
- Backend dev / sysadmin for almost two decades
- Developing Certbot @ EFF
- Open source stuff: acme-dns, ffuf
TLS: not exactly new
years and TLS/SSL versions go by...
2010
- SSH has taken over. Nobody dares even to think doing tasks over rlogin / rsh
- Web was not so lucky. Only the most critical / banking infra uses HTTPS
People are trying to push it though

2012 - Let's Encrypt
Started by Josh Aas and Eric Rescorla from Mozilla, Peter Eckersley from EFF and J. Alex Halderman from University of Michigan.
The project was publicly announced in 2014.
2015 - Go live (BETA)
- ACME protocol draft was submitted to IETF in January
- ISRG Root X1 generated in June
- First certificate signed by Let's Encrypt intermediate: "helloworld.letsencrypt.org" October 14th
- Let's Encrypt intermediate cross-signed by IdenTrust
- Public beta starts in December 3rd!
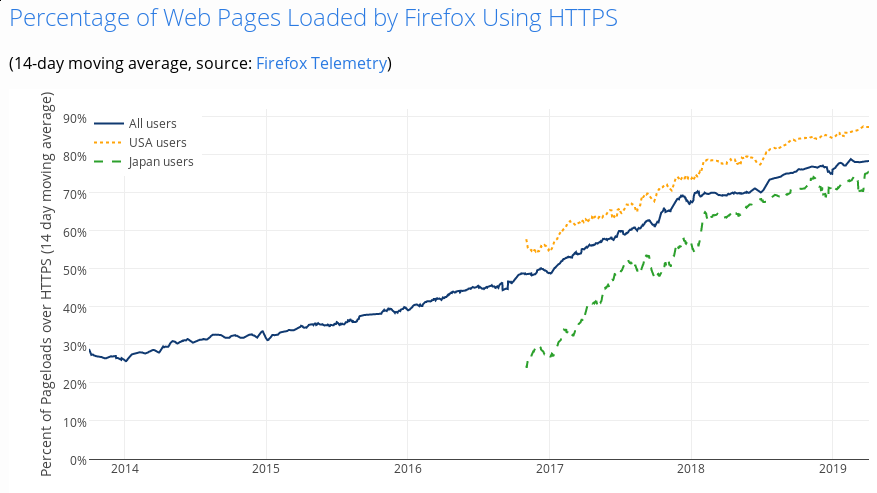
- Roughly 30% of web requests made over HTTPS
Background
- Let's Encrypt - CA run by ISRG
- ACME - Protocol
- Certbot - Client software developed by EFF
Benefits
Let's Encrypt and ACME
- Automatable
- Free of charge
- Open & Transparent
Importance of transparency and automation

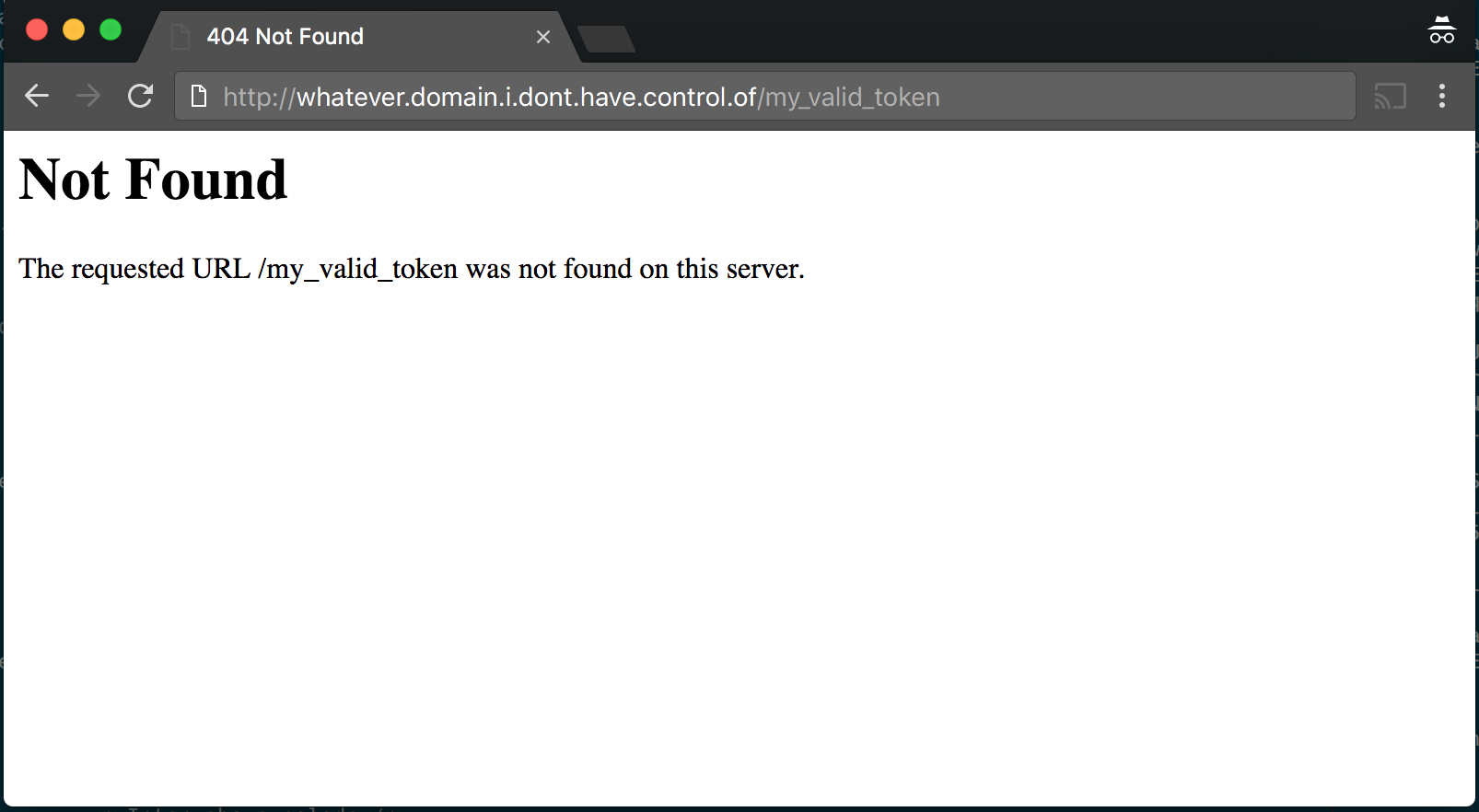
What could go wrong? part 1: 404
- GoDaddy HTTP validation picks up validation string from any part of body, regardless of HTTP status code
- Almost 9000 certificates revoked as precautionary measure.
What could go wrong? part 2: OCR
- .eu, .be, .at and some other TLDs don't provide whois information as text, but as an image instead, to deter spambots...
- Comodo using OCR to dig admin email from image...
- ...altelekom.at interpreted as a1telekom.at...
- ...misissued certificate for a1telekom.at
- Found by Florian Heinz and Martin Kluge
What could go wrong part 3: RAs
- Symantec had a Registration Authority program in place, allowing companies in the program to independently issue certificates under Symantec intermediates
- Not a problem itself, but responsibility stays with Symantec...
- ...for misissuances for unvalidated domain names
- ...for typos in domain names
- ...for bogus ST, L, O and OU fields
- Potentially 30 000 certificates affected
Social engineered revocation
- Hanno Böck registered two test domains, and obtained certificates for them from Symantec
- He created forged private keys for them, and posted the keys to pastebin
- Reported to Symantec, and got them revoked
- Symantec tried to hide the reason for (mis)revocation
What could go wrong? part 4: StartCom / WoSign
Uhh...
- Any port for validation
- Certificates using SNI with subdomain.domain.tld and domain.tld, only subdomain.domain.tld was validated
- Able to add arbitrary domains to request after validation
- Backdated SHA-1 certificates (after 1.1.2016)

- Short certificate lifetime - 90d
- Only DV certificates
- Some limitations in place
- Speaks ACME

- IETF standard, RFC 8555
- JSON over HTTPS
- Has it all: accounts, TOS, challenges, etc.
- Challenge types: HTTP, DNS,
and TLS-SNI, TLS-ALPN (2018)
- ACME client software
- Manages acquirance, renewal and revocation
- (Optionally) Configures secure TLS settings for you
- (Optionally) Helps to configure security enhancements
2016
- Public beta ends in April, with almost 2 million signed certificates
- Certbot (formerly known as "letsencrypt") gets its name
- Rapid growth. 20 million active certificates at the end of the year
- Alpha version of Nginx plugin in Certbot
- 46% of web requests made over HTTPS
2017
- 100 million certificates issued!
- At the end of the year 46 million unexpired certificates serving 61 million domains
- 58% of web requests made over HTTPS
2018
- ACME v2 and wildcard support going live in
January,February, March - ...but we have an issue on our hands...
2018
- ACME v2, wildcard support and DNS validation
- TLS-SNI challenge type disabled, and removed from ACME draft
- TLS-ALPN challenge type added
- 77% of web requests made over HTTPS
2019
- TLS-SNI turned off completely
- ACME protocol is now internet standard! RFC 8555
- Upcoming: multiple perspective validation
- Upcoming: CAA extensions (hopefully)
- Upcoming: Certbot Windows support
Currently
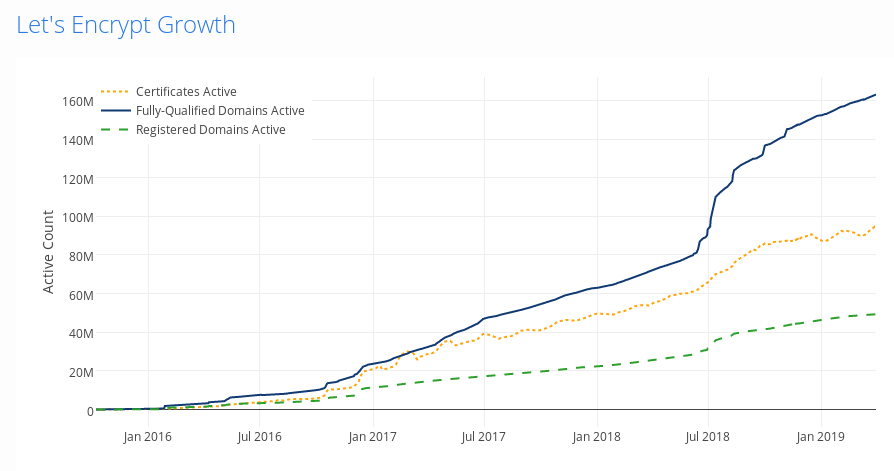
That's not all folks
- ACME getting adopted by other CA's! Buypass AS everyone!
- STARTTLS everywhere project is trying to bring mail infrastructure up to speed
- MTA-STS is now internet standard! RFC 8461
From this
To HTTPS demanded per default
Thanks!
@joohoi : https://1o.fi